Page History
...
| Info | ||
|---|---|---|
| ||
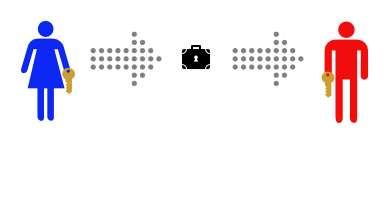
Simplified Example of asymmetric cryptography in practice: This is a story about Alice and Bob. Alice wants to send a private message to Bob, and the only easy way they have to communicate is via postal mail. Unfortunately, Alice is pretty sure that the postman is reading the mail she sends. That makes Alice sad, so she decides to find a way to send messages to Bob without anyone else being able to read them.
This time, Alice and Bob don’t ever need to meet. First Bob buys a padlock and matching key. Then Bob mails the (unlocked) padlock to Alice, keeping the key safe. Alice buys a simple lockbox that closes with a padlock, and puts her message in it. Then she locks it with Bob’s padlock, and mails it to Bob. She knows that the mailman can’t read the message, as he has no way of opening the padlock. When Bob receives the lockbox he can open it with his key, and read the message. This only works to send messages in one direction, but Alice could buy a blue padlock and key and mail the padlock to Bob so that he can reply. Or, instead of sending a message in the padlock-secured lockbox, Alice could send Bob one of a pair of identical keys. Then Alice and Bob can send messages back and forth in their symmetric-key lockbox, as they did in the first example. |
Encryption for secure communication
...
You can use the previously discussed encryption methods to securely encrypt and send private information, but they maybe too cumbersome to use if you only want to prevent eavesdropping while the data is in transit. If the information doesn't have to remain encrypted once it reaches its target, there's a far better approach: Perfect Forward Secrecy (PFS). PFS is designed for ongoing communication (like your web-browser communicating with a website over a browsing session, or a messaging application), it works in a very similar way to the previously discussed encryption methods, but it differs in that it generates a unique key-pair for every subsequent communication, this insuring that even in the unlikely event that an attacker can guess a key, they can that one message - leaving the rest of the communication session private and secure.
The Signal messaging protocol employs perfect forward secrecy, and when implemented properly, it is the most secure way to privately send messages. Keep in mind that once the messages are decrypted by the messaging application, they sit on the receiver's device en-encrypted.
We recommend the following messaging applications for secure and private communication:
- Signal Private Messenger (Android: https://play.google.com/store/apps/details?id=org.thoughtcrime.securesms, iOS: https://itunes.apple.com/us/app/signal-private-messenger/id874139669?mt=8)
- WhatsApp (Android: https://play.google.com/store/apps/details?id=com.whatsapp, iOS: https://itunes.apple.com/us/app/whatsapp-messenger/id310633997?mt=8)
- Google Allo (in incognito mode): (Android: https://play.google.com/store/apps/details?id=com.google.android.apps.fireball, iOS: https://itunes.apple.com/us/app/google-allo/id1096801294?mt=8)
- Keep in mind, that Google Allo only employs the signal protocol during incognito sessions, but this has the added benefit of easily deleting the conversation when it's read, removing the risk of it sitting un-encrypted.
- Skype and Facebook Messenger both have a Private Conversation mode, which switches to a session protected by the Signal Protocol, but the default chat mode is not.