Page History
This is a simplified guide to encryption, security, and digital privacy. the programs and tools recommended here are tested and trusted by the us, but they are not the only suitable option. The goal of this write-up is to guide you towards the best level of privacy without adding unnecessary complications, to strike a balance between a solution that's "good enough" and easy to use.
...
For software based token authentication, we recommend LastPass Authenticator (https://lastpass.com/auth/). If used in conjunction with LastPass password manager, it allows you to securely and easily backup your authentication codes in your LastPass vault, making it easy to recover access to all your accounts in case your phone gets lost or damaged.
Anti Virus
Encryption
We'll describe three types of encryption technologies/algorithms we recommend, and go into detail on how and when to utilize each.
...
Advantages:
- Easy to use
- Does not rely on trusting a third party
- Suitable for encrypting data for secure storage
Disadvantages:
- Not suitable for sharing sensitive information
Technology overview:
Advanced Encryption Standard (AES) is a symmetric key algorithm ratified as a standard by the National Institute of Standards and Technology of the United States; AES-256 is currently labeled as sufficient to use in the US government for the transmission of TOP SECRET information.
At present, there is no known practical attack that would allow someone without knowledge of the key to read data encrypted by AES when correctly implemented. As far as we know, intelligence organizations such as the NSA are not able to break it.
A symmetric block cipher uses a single encryption key to encrypt and to decrypt a file, making it useful to encrypt personal documents but useless for sharing sensitive information with a third party.
Antivirus
...
Modern operating systems are designed with security in mind, and modern web browsers are very good at telling us when a website seems risky, but at the end of the day the computer will do what we tell it, and if we accidentally tell it to trust an infected file, antivirus can act as a last resort to stop the spread of the infection. The key takeaway here is that we want antivirus to be a last resort, just in case, we shouldn't solely rely on it for safety and security.
- All Operating Systems are vulnerable to some degree
Don't believe the common myth that a specific OS is impenetrable, malware can affect all kinds of consumer operating systems.
However, all modern operating systems have built in features that protect against the most common types of malware, and they may never get infected as long as we are careful when using them. Again I stress that antivirus should be a last resort, you want your antivirus to be there if you make a mistake, but our goal is to never need to use it. Do use an antivirus program, but also finish reading this section.
As of June 2018, we recommend these Antivirus programs, for their consistently high catch rate (percentage of threats neutralized) and low false catch rate (false alarms that inconveniently block safe programs), as well as low usage of system resources:- For Windows:
- Bitdefender (https://www.bitdefender.com/)
- ESET(https://www.eset.com/us/)
- For Mac OS
- Bitdefender (https://www.bitdefender.com/)
- Trend Micro (https://www.trendmicro.com/en_us/business.html)
- AV Test Institute (https://www.av-test.org/en)
- AV-Comparatives (https://www.av-comparatives.org)
- Use common sense
- Keep your software up to date, always install security updates when they are available. Update address critical vulnerabilities in your operating system and applications, keeping software up to date is the easiest and most effective method of securing it.
- Know what software you're running!
- Don't grant administrative access to applications you don't trust. Always read dialog boxes that your operating system presents you!
- Pay attention to the permissions an app is requesting on your phone, do they make sense for what the app is supposed to do?
- Avoid risky websites. Look for obvious signs like promising paid content for free, brand name products for sale at prices too good to be true, etc.
- Keep an eye out for popups that warn you that your computer is damaged, if it's not coming from your antivirus software, it's fake.
- Never grant remote access to your computer to unsolicited callers. Microsoft/Apple will never call you about problems with your computer.
- Use a good ad-blocker to minimize your exposure to potential scams. We recommend uBlock Origin for Google Chrome (https://chrome.google.com/webstore/detail/ublock-origin/cjpalhdlnbpafiamejdnhcphjbkeiagm?hl=en)
- Don't open any attachments from unknown and unsolicited senders.
- Even if you trust the sender, exercise common sense when opening attachments. Read message boxes carefully, if an application like Microsoft Word for example, is informing you that it's opening the attachment in "Protected View" and to "be careful", while the attachment itself is telling you to disable protected view, trust your application.
- Never share your personally identifiable information with unsolicited callers/emails.
- Businesses (Apple, your bank, power company, etc) will never ask you to share your password with them.
- If a business you deal with calls you and asks you to verify your personal information, politely inform them that you're going to hang up and call back; this is standard practice and they should be trained to expect that. Call the business on their main line and confirm that they were the ones calling you.
- Be careful when clicking on links in emails, it may not be the real website of the business, but a fake copy of it. Never type your password into a website if you don't recognize the address, even if it looks like the real thing.
- You can use the browser extension Web Of Trust to help you identified trusted websites (https://www.mywot.com/en/download)
- Backup and Recovery
The most common and profitable malware today is known as ransomware, once they convince you to execute the infected file, the virus starts encrypting files on the computer and gives you a specific period of time to pay a ransom to decrypt your files. The attacker often has no motivation, intention, or ability to decrypt your files, even after paying the requested ransom. The best way to recover from this type of attack is to restore from a clean backup; this also holds true for any cause of data-loss.- Backup
Backup any and all files you wouldn't be able to replace: important documents, family photos and videos, or any other irreplaceable data. - Backup often
Backup your files often as they are modified or updated. - Backup smart
Use the 3-2-1 backup strategy to insure the safety of your data. Always keep at least 3 copies of all data you cannot replace, on at least 2 devices, with at least 1 copy stored off-site.
For example, keep your data on your laptop computer, store a copy on a portable hard drive, and upload the rest to a cloud backup service.
For cloud backups, we recommend Backblaze (https://www.backblaze.com), they offer unlimited backups for $5/month, all your files are encrypted locally and they offer the option to provide your own private encryption key (see Encryption section), meaning you control the encryption and they cannot decrypt your data on their end.
- Backup
Encryption
Encryption is the process of scrambling data through complicated mathematical formulas that make them unrecognizable, we'll discuss three use-cases for encryption, and the types of encryption and tools for each use-case.
Personal Encryption
...
For encrypting personal data for long term storage and/or secure off-site backup, we recommend using AES. Advanced Encryption Standard (AES) is a symmetric key algorithm ratified as a standard by the National Institute of Standards and Technology of the United States; AES-256 is currently labeled as sufficient to use in the US government for the transmission of TOP SECRET information.
At present, there is no known practical attack that would allow someone without knowledge of the key to read data encrypted by AES when correctly implemented. As far as we know, intelligence organizations such as the NSA are not able to break it.
A symmetric block cipher uses a single encryption key to encrypt and to decrypt data, making it useful to encrypt personal documents but useless for sharing sensitive information with a third party.
AES is:
- Easy to use
- Does not rely on trusting a third party
- Suitable for encrypting data for secure storage
Once properly encrypted, data can safely be duplicated for off-site backups or removal from local device.
The tool we recommend using for encrypting personal files is 7-zip
...
Advantages:
- Suitable for sharing private information
- Suitable for encrypting data for secure storage
- Depending on implementation:
- Does not rely on trusting a third party with decryption keys - with manual implementation (as described in this write-up)
- Easy to use - with delegated implementation (with services like protonmail.com)
Disadvantages:
- Depending on implementation:
- Difficult to learn, tedious to use - with manual implementation (as described in this write-up)
- Relies on trusting a third party - with delegated implementation (with services like protonmail.com)
Technology overview:
RSA is a public-key cryptosystem, which uses an asymmetric key algorithm. The most important concept to understand about asymmetric key encryption is that it uses a public-private key pair, the public key is used to encrypt data, and the private key is used to decrypt it.
This allows you to share the public key freely, which a sender would use to enrypt their data before sending to you, and only you can decrypt the data with your private key. In contrast, when you want to send sensitive data to another person, you must use their public key to encrypt it.
At present, there is no known practical attack that would allow someone without knowledge of the private key to read data encrypted by RSA when correctly implemented. As far as we know, intelligence organizations such as the NSA are not able to break it.
Advantages:
- Easy to use
- Suitable for sharing private information
- Does not rely on trusting a third party
- For some implementations, can be used to easily send private messages without leaving any traces of them anywhere.
Disadvantages:
- Not suitable for encrypting data for secure storage
- Tied to phone number, phone line must be active and capable of receiving incoming messages to reinstall application
- Does not keep encrypted backup, either relies on external unencrypted backup or loses all past communications.
Technology Overview:
Signal is similar to
Simplified Example of symmetric cryptography in practice:
Taken from https://wordtothewise.com/2014/09/cryptography-alice-bob/
This is a story about Alice and Bob.
Alice wants to send a private message to Bob, and the only easy way they have to communicate is via postal mail.
Unfortunately, Alice is pretty sure that the postman is reading the mail she sends.
That makes Alice sad, so she decides to find a way to send messages to Bob without anyone else being able to read them.
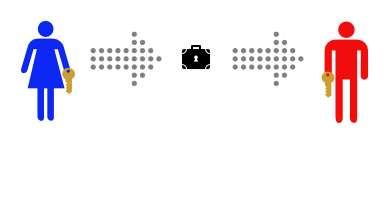
Alice decides to put the message inside a lockbox, then mail the box to Bob. She buys a lockbox and two identical keys to open it. But then she realizes she can’t send the key to open the box to Bob via mail, as the mailman might open that package and take a copy of the key.
Instead, Alice arranges to meet Bob at a nearby bar to give him one of the keys. It’s inconvenient, but she only has to do it once.
After Alice gets home she uses her key to lock her message into the lockbox.
Then she sends the lockbox to Bob. The mailman could look at the outside, or even throw the box away so Bob doesn’t get the message – but there’s no way he can read the message, as he has no way of opening the lockbox.
Bob can use his identical key to unlock the lockbox and read the message.
This works well, and now that Alice and Bob have identical keys Bob can use the same method to securely reply.
Meeting at a bar to exchange keys is inconvenient, though. It gets even more inconvenient when Alice and Bob are on opposite sides of an ocean.
...
Simplified Example of asymmetric cryptography in practice:
Taken from https://wordtothewise.com/2014/09/cryptography-alice-bob/
This is a story about Alice and Bob.
Alice wants to send a private message to Bob, and the only easy way they have to communicate is via postal mail.
Unfortunately, Alice is pretty sure that the postman is reading the mail she sends.
That makes Alice sad, so she decides to find a way to send messages to Bob without anyone else being able to read them.
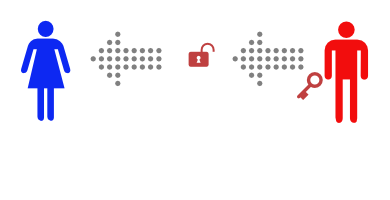
This time, Alice and Bob don’t ever need to meet. First Bob buys a padlock and matching key.
Then Bob mails the (unlocked) padlock to Alice, keeping the key safe.
Alice buys a simple lockbox that closes with a padlock, and puts her message in it.
Then she locks it with Bob’s padlock, and mails it to Bob.
She knows that the mailman can’t read the message, as he has no way of opening the padlock. When Bob receives the lockbox he can open it with his key, and read the message.
This only works to send messages in one direction, but Alice could buy a blue padlock and key and mail the padlock to Bob so that he can reply.
Or, instead of sending a message in the padlock-secured lockbox, Alice could send Bob one of a pair of identical keys.
Then Alice and Bob can send messages back and forth in their symmetric-key lockbox, as they did in the first example.
...
When to use AES:
To encrypt your whole computer, or to encrypt files on the computer, which you don't intend to share with anyone.
...
When to use RSA:
To encrypt sensitive information for sharing with a third party, primarily through email. You can also use your own public key to encrypt your own files as you would with AES, but it adds a few steps to the process.
...
A concise guide on using the recommended tools will be added soon, but a more detail tutorial for using each tool can be found on their respective websites.
AES
Once properly encrypted, the files can safely be duplicated for off-site backups or removal from local device.
The tool I recommend using for encrypting personal files is 7-zip (https://www.7-zip.org/). 7-Zip is a free and open source compression and packaging program with a strong implementation of AES-256 encryption.
For MacOS X, Keka (https://www.keka.io/en/) is a port of 7-zip that offers the same level of encryption. A guide for using Keka can be found here: https://github.com/aonez/Keka/wiki/Compressing-with-Keka
What's great about We recommend 7-zip because it is that it's a very popular archiving tool, and it doesn't scream "I'm encrypting files!", satisfying the Security-through-obscurity principal.
For a more convenient - but less obscure - experience, I recommend recommend VeraCrypt (https://www.veracrypt.fr/en/Home.html). It allows you to mount a logical drive (think a USB drive plugged into your computer), where everything you save to the drive is encrypted. You can then safely upload the whole volume (or "drive" file).
RSA
. You can then safely upload the whole volume (or "drive" file).
| Info | ||
|---|---|---|
| ||
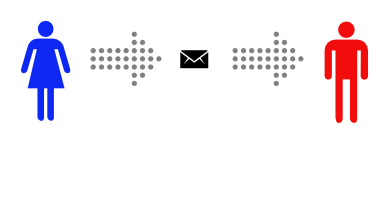
Simplified illustration of symmetric cryptography in practice: This is a story about Alice and Bob. Alice wants to send a private message to Bob, and the only easy way they have to communicate is via postal mail. Unfortunately, Alice is pretty sure that the postman is reading the mail she sends. That makes Alice sad, so she decides to find a way to send messages to Bob without anyone else being able to read them.
Alice decides to put the message inside a lockbox, then mail the box to Bob. She buys a lockbox and two identical keys to open it. But then she realizes she can’t send the key to open the box to Bob via mail, as the mailman might open that package and take a copy of the key. Instead, Alice arranges to meet Bob at a nearby bar to give him one of the keys. It’s inconvenient, but she only has to do it once. After Alice gets home she uses her key to lock her message into the lockbox. Then she sends the lockbox to Bob. The mailman could look at the outside, or even throw the box away so Bob doesn’t get the message – but there’s no way he can read the message, as he has no way of opening the lockbox. Bob can use his identical key to unlock the lockbox and read the message. This works well, and now that Alice and Bob have identical keys Bob can use the same method to securely reply. Meeting at a bar to exchange keys is inconvenient, though. It gets even more inconvenient when Alice and Bob are on opposite sides of an ocean. |
Encryption for secure data sharing
...
For encrypting data for the purpose of sharing it with others, we recommend using RSA. RSA is a public-key cryptosystem, which uses an asymmetric key algorithm. The most important concept to understand about asymmetric key encryption is that it uses a public-private key pair, the public key is used to encrypt data, and the private key is used to decrypt it.
This allows you to share the public key freely, which a sender would use to encrypt their data before sending to you, and only you can decrypt the data with your private key. In contrast, when you want to send sensitive data to another person, you must use their public key to encrypt it.
At present, there is no known practical attack that would allow someone without knowledge of the private key to read data encrypted by RSA when correctly implemented. As far as we know, intelligence organizations such as the NSA are not able to break it.
RSA is:
- Suitable for sharing private information
- Suitable for encrypting personal data for secure storage
Depending on implementation:
Delegated implementation (with services like protonmail.com):- Relies on trusting a third party
- Easy to use
- Difficult to learn and tedious to use
- Does not rely on trusting a third party with decryption keys
When sharing sensitive information, such as passwords or private encryption keys, always insure the data is encrypted end-to-end; that is, encrypted on the sender's local device, and decrypted on the receiver's local device.
Services like protonmail.com rely on public-key encryption to insure your emails are encrypted end-to-end, but to make it easy to use, they hold on to your private key and store it securely in their own servers. The private key is itself encrypted on their servers and is only decrypted when you successfully login to your account, it is then decrypted and sent to your browser where it is stored in memory to decrypt the emails. In theory, ProtonMail cannot access your private key, but since we don't know how they encrypt it, we cannot know for sure that it's securely encrypted. Therefore, we rely on them to not access it or allow anyone else to access it. For most communications, ProtonMail is considered highly secure.
It's important to note that emails sent through proton mail are only end-to-end encrypted when sent to a proton mail recipient. This is our unlisted ProtonMail account if you wish to reach us through it: quietwizard@protonmail.com
For the ultimate security and privacy, we must manually encrypt our data.
For Windows:
Creating the private-public keypair
For computers running on the Windows Operating System, we're going to use Gpg4Win (https://www.gpg4win.org/) a free and Open Source suite of tools for email and file encryption.
After installing the Gpg4Win suite, the first thing we need to do is create the key pair. It consists of a public key used to encrypt data, and a private key used to decrypt data encrypted with the public key.
To create a key pair, launch Kleopatra and choose "New Key Pair" from the File menu:
Choose the "Create a personal OpenPGP key pair option:
Although it says optional for both, the program requires some text to be entered for either the Name or Email fields, feel free to just enter anything in the name field if you don't wish to disclose your name.
Click on the Advanced Settings button, and make sure you're using RSA 4096 bits, the checkbox for "+RSA" is optional, and can be used for signing, go ahead and check it.
The next step is to choose a password, create a unique and secure password for your key pair.
Once your key is generated, make a backup of your key pair by clicking the appropriate button
When prompted, save the file to a secure storage location.
You can now hit finish, and you'll see your certificates listed:
From here, you can right click on your certificate to export your private (or secret) key. Be very careful when doing so, remember this key is used to decrypt your data, and it must be stored securely. Make sure you encrypt your exported private key with AES before storing it long-term.
Now right click on your newly created certificate and click on "Export." Choose a place to save the file and give it a name, and hit save. This is your public key, you share this key freely, people would use this key to encrypt messages sent to you, and only you can decrypt those messages using your private key. Go ahead and send us your public key, we will use it to communicate sensitive information with you.
This is our public key, if you wish to send us encrypted data, use this key to encrypt the data: FA54269DC1F06A818DD21FE3F36C4AF0A737AAEA.asc (download the file, and double click it to import it into your Kleopatra certificate cache).
Encrypting data:
The Gpg4Win suite has added new options to your windows context menu (when you right click on a file)
When you click on "Sign and encrypt" or "Encrypt", you're presented with Kleopatra's encryption dialog:
Signing is optional, and you sign with your key pair if you chose the +RSA option. When encrypting for personal use, you can use your key pair to encrypt, but when encrypting to send to someone, you choose the public-key of the recipient which we imported earlier.
Note that we unchecked the "Encrypt for me" option, since we're using the public key of the recipient. We checked "Encrypt for others" option and chose the imported public key by searching for the name on the key ("XXXXX").
The encrypted file is saved in the same directory as the original file, by default. You can choose another location if you'd like. You can now send the encrypted file knowing that no one can read its contents except the intended recipient (the owner of the public key).
The Gpg4Win suite has also installed extensions to allow you to easily encrypt/decrypt emails within Outlook, if you happen to have that installed.
| Info | ||
|---|---|---|
| ||
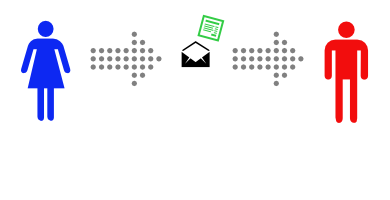
Simplified Example of asymmetric cryptography in practice: This is a story about Alice and Bob. Alice wants to send a private message to Bob, and the only easy way they have to communicate is via postal mail. Unfortunately, Alice is pretty sure that the postman is reading the mail she sends. That makes Alice sad, so she decides to find a way to send messages to Bob without anyone else being able to read them.
This time, Alice and Bob don’t ever need to meet. First Bob buys a padlock and matching key. Then Bob mails the (unlocked) padlock to Alice, keeping the key safe. Alice buys a simple lockbox that closes with a padlock, and puts her message in it. Then she locks it with Bob’s padlock, and mails it to Bob. She knows that the mailman can’t read the message, as he has no way of opening the padlock. When Bob receives the lockbox he can open it with his key, and read the message. This only works to send messages in one direction, but Alice could buy a blue padlock and key and mail the padlock to Bob so that he can reply. Or, instead of sending a message in the padlock-secured lockbox, Alice could send Bob one of a pair of identical keys. Then Alice and Bob can send messages back and forth in their symmetric-key lockbox, as they did in the first example. |
When sharing sensitive information, such as passwords or private encryption keys, always insure the data is encrypted end-to-end; that is, encrypted on the sender's local device, and encrypted on the receiver's local device. The use of public-key encryption is most commonly used not limited to